8 Min Read |16 May 2024 | Key Words: SSH, Encryption, Remote server access, Public key authentication
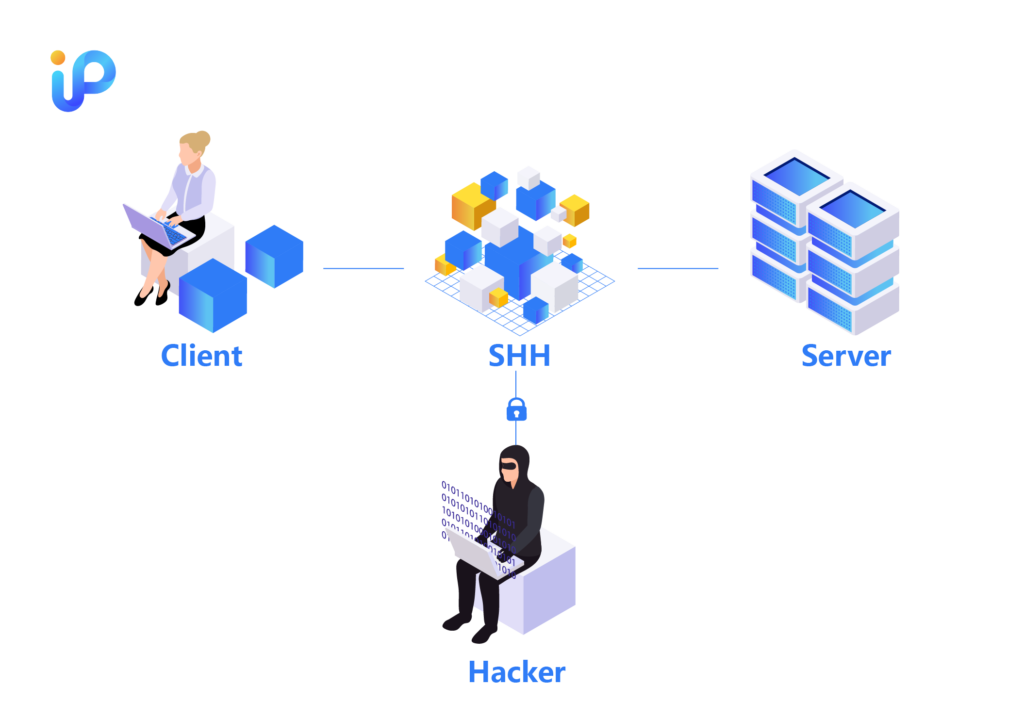
In the realm of digital communication, SSH (Secure Shell Protocol) plays a pivotal role. As a widely used network protocol, SSH primarily handles two critical tasks: safeguarding the security of network communications and encrypting data sharing. In today’s challenging online landscape, SSH stands out for its encryption capabilities, offering a formidable defense for data safety during transmission. But how do we understand SSH, and how does it achieve these functionalities?
SSH is more than just a term, it represents a comprehensive mechanism consisting of a specific encryption network protocol and associated implementation programs. This powerful tool enables both network administrators and regular users to securely access remote systems while maintaining security in an imperfectly secure network environment. It provides a means to ensure the safety and privacy of data transmissions while managing servers remotely.
The security capabilities of SSH extend beyond establishing an encrypted transmission channel; they also include a multi-layer authentication process, such as strong password authentication and public key authentication, ensuring that only authorized users can gain access. Therefore, SSH protocol and SSH keys play a vital role in guarding network security, be it for file transfers, system maintenance, or automation tasks.
How does SSH work?
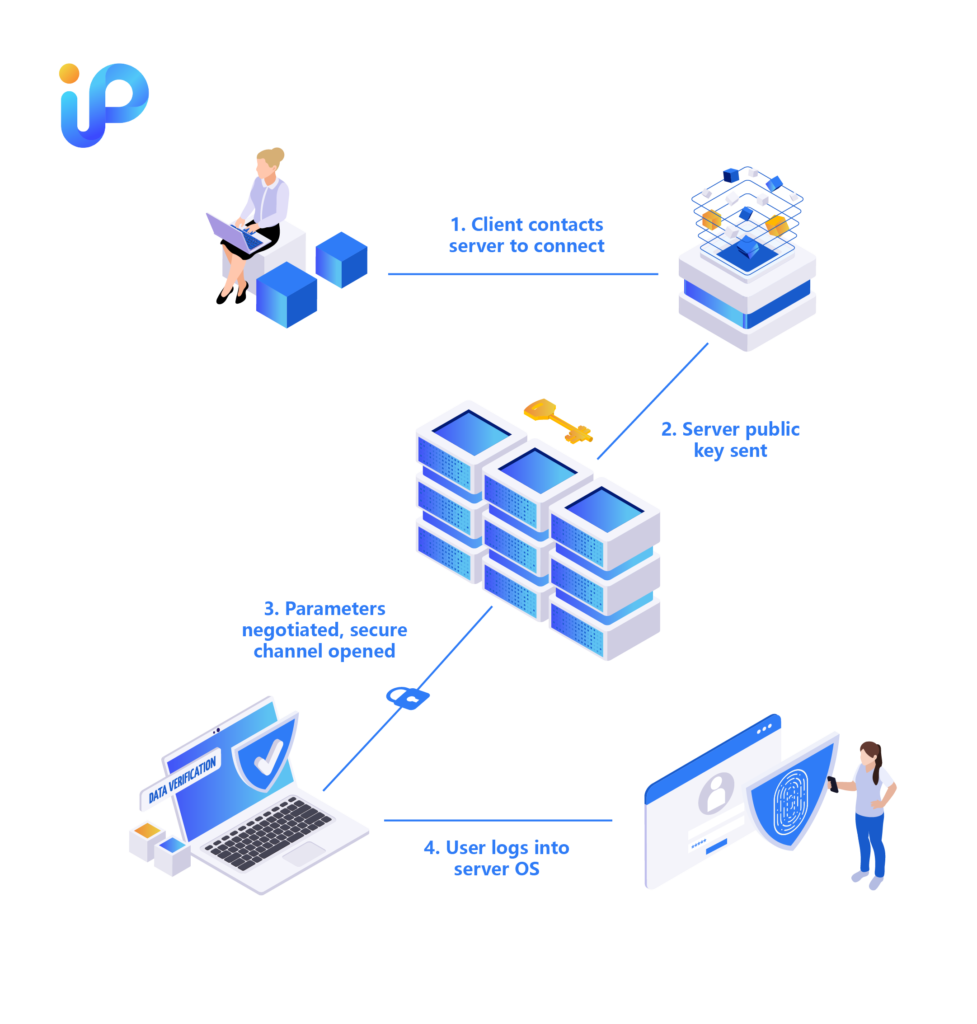
SSH functions as a secure information highway by employing a client-server model to connect applications with servers or to link the location where a session is displayed with its actual running location. Imagine the SSH client as an information messenger, proactively establishing contact with the SSH server to initiate a journey of secure communication. During this process, the SSH server presents its “identity card” in the form of a public key. Utilizing the art of public-key cryptography, the client verifies the server’s identity to ensure the authenticity of communication.
Once the identity is confirmed, the SSH protocol acts like a professional bodyguard, employing robust symmetric encryption protocols and hash algorithms to create a private and secure environment for data transmission. Within this environment, the exchange of data between the client and server becomes both secure and efficient.
To achieve this, SSH clients and servers use various encryption methods, with Blowfish and Advanced Encryption Standard (AES) being the most common. Blowfish, an older method of encryption, still has its unique applications in certain scenarios. Meanwhile, AES, a more modern encryption technology developed by the National Institute of Standards and Technology, is widely used to protect billions of data worldwide.
It is worth noting that the SSH secure connection varies across different operating systems:
- On Mac and Linux – via Terminal
- On Windows – via an installed SSH client
The client-server relationship can be tricky to understand. Let’s delve into how both SSH servers and SSH clients function to shed light on this matter.
SSH server
SSH servers are key components that facilitate secure network connections through TCP port 22. These servers employ a combination of public and private key encryption technology to authenticate their identity during the setup of each SSH connection, ensuring that communication with clients is both secure and dependable.
This secure connection allows users to perform a variety of operations, including but not limited to:
- Secure file transfer.
- Remote command execution.
- Remote host management.
Given that SSH servers provide a gateway for remote access to host systems, they often become targets of network attacks. Therefore, running high-quality software and strictly adhering to security protocols is crucial for SSH servers to prevent potential vulnerabilities.
SSH client
To establish secure connections between local and remote computers, system administrators often install specific software, known as Secure Socket Client. Operating systems like Mac and Linux typically come with built-in SSH server capabilities, while Windows might require the installation of specialized software such as OpenSSH or similar tools. Once the SSH server is installed on the remote computer, it can accept secure connection requests from an SSH client, providing administrators with a secure alternative to traditional remote access methods.
The operation of an SSH server involves providing a secure environment when a connection request is initiated from the local computer via the client, enabling administrators to securely connect to the remote host. For SSH authentication, administrators can use a username and password to confirm their identity, or opt for a more secure method using public-private key pairs which allows for password-less remote access management.
Encryption key
SSH keys are a critical technology in network security, offering a higher level of protection compared to traditional password authentication. This key mechanism is particularly useful in automated scenarios, such as seamless file transfers without human intervention, and remote system management.
This key-based authentication method comprises two parts: the public key and the private key. The public key is stored on the server, while the corresponding private key is kept by the user. Only the correctly matched private key can unlock the information encrypted by the public key.
However, a notable concern arises from the fact that many enterprises fail to set additional passwords for their SSH keys, potentially compromising security. Therefore, it is recommended to regularly change keys, strengthen password protection for private keys, and use key management tools to enhance key security. Implementing these measures helps maintain a more robust network environment.
What is SSH used for?
SSH (Secure Shell) serves various purposes and plays a crucial role in automation and data security. Some of its key uses include:
- Remote Server Access and Management
SSH allows network administrators to securely log in to remote servers and manage them from a distance. It provides a secure command-line interface for executing remote commands and performing system administration tasks. - Encrypted Data Transmission
SSH ensures secure and encrypted data transmission between client and server. It protects data integrity and confidentiality, making it an ideal choice for transmitting sensitive information over untrusted networks. - Secure File Movement (SSH is more secure than unencrypted protocols like FTP)
SSH provides secure file transfer capabilities, surpassing the security of unencrypted protocols like FTP. It enables secure file uploads, downloads, and transfers between systems, protecting data during transit. - Automation of Tasks
SSH plays a significant role in automating various tasks and workflows. It allows for remote execution of commands and scripts, making it easier to automate routine tasks such as backups, report generation, data archiving, and system maintenance. - Port Forwarding and Tunneling
SSH supports port forwarding and tunneling, allowing users to securely access services and resources on remote networks. It enables the creation of encrypted tunnels that protect data while accessing internal resources or bypassing network restrictions.
What Role Does SSH Play in Automation and Data Security?
The SSH network protocol plays multiple roles in data centers: In Mac, Unix, and Linux operating systems, it acts as a secure key for network administrators to remotely log in and manage systems; during application testing and system reboots, it serves as a reliable safeguard ensuring smooth operations; and in data transmission, it supports crucial automated processes.
In large enterprise environments, the role of SSH is similarly multifaceted and vital: It elevates the security level of file transfers, solidifying them through the SFTP protocol developed by the Internet Engineering Task Force (IETF); it also optimizes a variety of operational tasks through automation, including report generation, system and data backups, data archiving, database maintenance, and network management.
For small businesses, SSH provides a secure channel for sharing files with clients, safeguarding the data of both parties.
In summary, SSH acts as a solid foundation for building encrypted connections for organizations of all sizes. It contributes to data security and privacy across a range of scenarios, including system administration, enterprise automation, and secure file sharing. From system administrators to enterprise users, and even ordinary individuals, the applications of SSH are extensive and significant.
Are there any security risks associated with SSH?
While SSH is known for its strong security, it is not immune to security risks. The primary issue lies in the management of SSH keys. Inadequate key management practices, such as poor generation, storage, or revocation of keys, can create vulnerabilities and unauthorized access.
Additionally, misconfigurations of SSH servers and clients can expose systems to man-in-the-middle attacks or brute-force attacks. Given that SSH provides privileged access to systems, any compromise can result in data breaches or unauthorized control over enterprise resources.
Therefore, although SSH is inherently secure, it is essential to emphasize proper key management and configuration practices to ensure the robust protection of sensitive data.
How to Enhance SSH Security?
SSH (Secure Shell Protocol) is a critical component of enterprise network security. To counter growing cyber threats, businesses need to take steps to enhance the security of SSH. Here are four core strategies to improve SSH security:
- Key Lifecycle Management:
Implement a robust management system for SSH keys throughout their lifecycle. This includes regular key rotation to minimize the risk of compromised keys, updating keys when necessary, and disposing of keys that may have been leaked or are no longer needed.
- Strengthen Authentication Mechanisms:
Enhance the security level of SSH access by implementing multi-factor authentication to ensure only authorized users gain access.
- Strict Access Control and Minimal Privileges:
Enforce stringent access control measures for SSH, particularly for high-privilege accounts. Limit SSH access rights to only those users who require it for their specific roles and responsibilities. By minimizing privileges, you reduce the potential attack surface and mitigate the impact of any security breaches.
- Continuous Monitoring and Auditing: Maintain a comprehensive monitoring and auditing system for SSH sessions. Continuously monitor and analyze SSH activity logs to promptly detect any suspicious or unauthorized activities. Regularly review the logs to identify and address any security incidents or policy violations, ensuring the overall integrity of SSH connections.
By implementing these strategies, businesses can significantly enhance the security of their SSH infrastructure and safeguard their network from potential threats.